There are several factors to consider in the process of establishing, scaling and maintaining a modern business in today’s fast-paced corporate ecosystem. While the list of factors to consider in building a successful business are numerous, there is no doubt …
With a vision to provide added value to customers by way of its reliable one-stop-shop model for Information Technology (IT) services and solutions, CITSYS Limited empowers African businesses for growth by developing and delivering cutting edge technology-driven solutions for clients across sectors. This is particularly crucial in today’s evolving corporate landscapes with shifting …
Endpoints are the communication entry and exit point of an organisation’s network. Laptops, desktops, servers, mobile phones, tablets, and virtual environments can all be considered endpoints. These endpoints usually help in accomplishing daily business tasks like sending and receiving emails, …
Over the years, Apple devices have proven to be more secure than their Windows and Android cousins, as a PC user of many years, I vividly remember the cloak of invincibility that Apple users bragged about. They looked down on …
Customized Systems Development Dynamic Planner for Investments and Pensions Planning System Integration with Payment Gateways Port Billing Operation System Hospital Management System Casual Labor Management System Customer Relations Management System Human Resource Management System Speak to our experts to get …
Have you been hit by a serious cyber attack and are quickly looking for solutions or are you just getting to know about cyber security threats? Well, this latest blog post would inform and education you on the growing trend …
As the internet becomes more prevalent in our daily lives, it also becomes an increasingly popular destination for children. It’s important to be aware of what your child is doing online and how they are using their time on the …
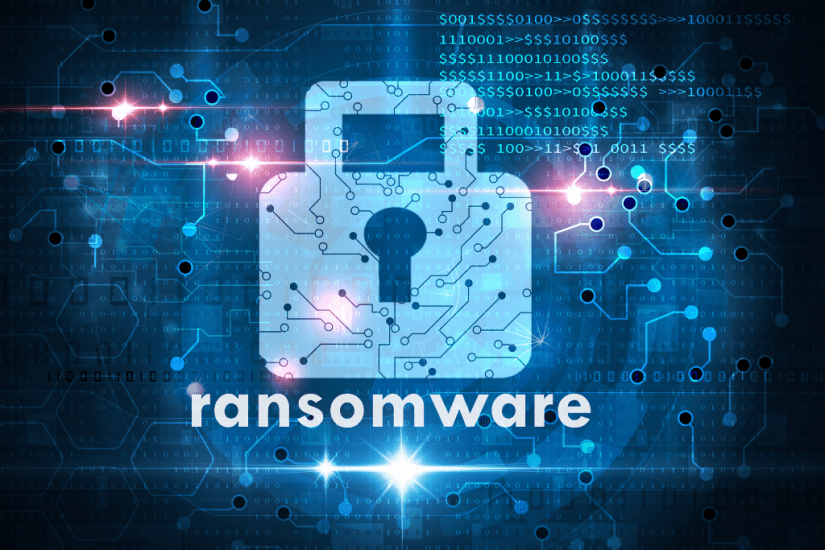
When you are attacked by ransomware or any encryption Trojan your data is encrypted, and your operating system is hijacked. Just like the concept of hostage and ransom, the ransomware holds your files as “digital hostage” and only releases them …
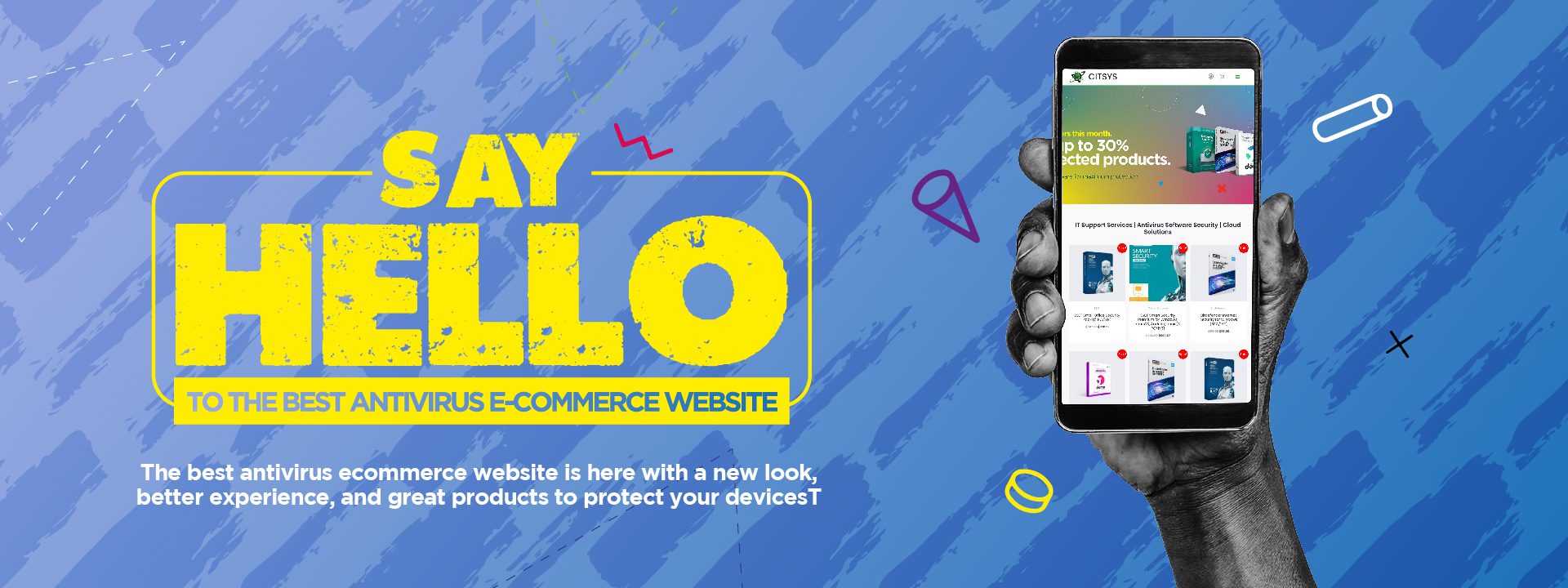
We are thrilled and excited to announce the launch of our newly designed website. Visit us at www.citsys.com. After several months of hard work and dedication, we are delighted to officially announce the launch of our new website. Our CEO …
With over 120 branches across Ghana, this leading financial institution serves a diverse customer base both – business to business (B2B) and business to customers (B2C) market segment. Banks and Financial institutions have long been a major target for cybercriminals …